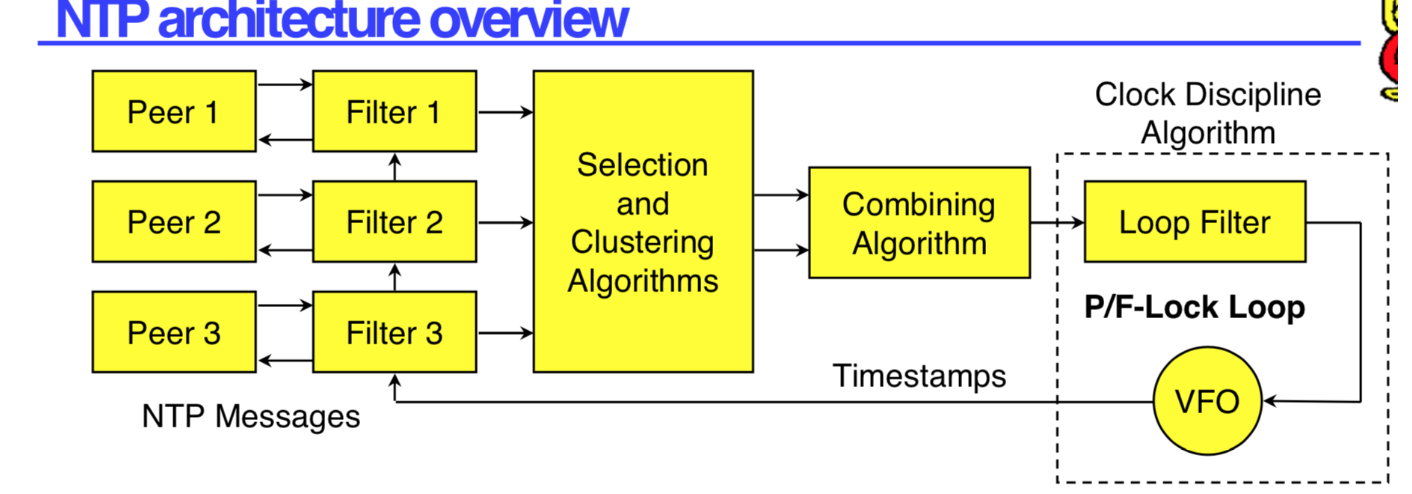
流程记录
- 软件包安装 并关闭SELinux
– 配置epel源,直接使用yum安装
yum install cobbler cobbler-web dhcp bind pykickstart tftp -y
- 需要注意dhcp/bind需要单独安装一下,cobbler没依赖dhcp/bind
sed -i 's#SELINUX=enforcing#SELINUX=disabled#g' /etc/selinux/config
setenforce 0
systemctl restart cobblerd
- 配置cobbler参数
– 修改/etc/cobbler/settings的参数
allow_dynamic_settings: 1
default_password_crypted: "$1$random-p$yqLCVPP/OBjIT02WekZic1"
next_server: 192.168.117.134
manage_dhcp: 1
manage_dns: 1
server: 192.168.117.134
manage_rsync: 1
pxe_just_once: 1 #防止循环装机
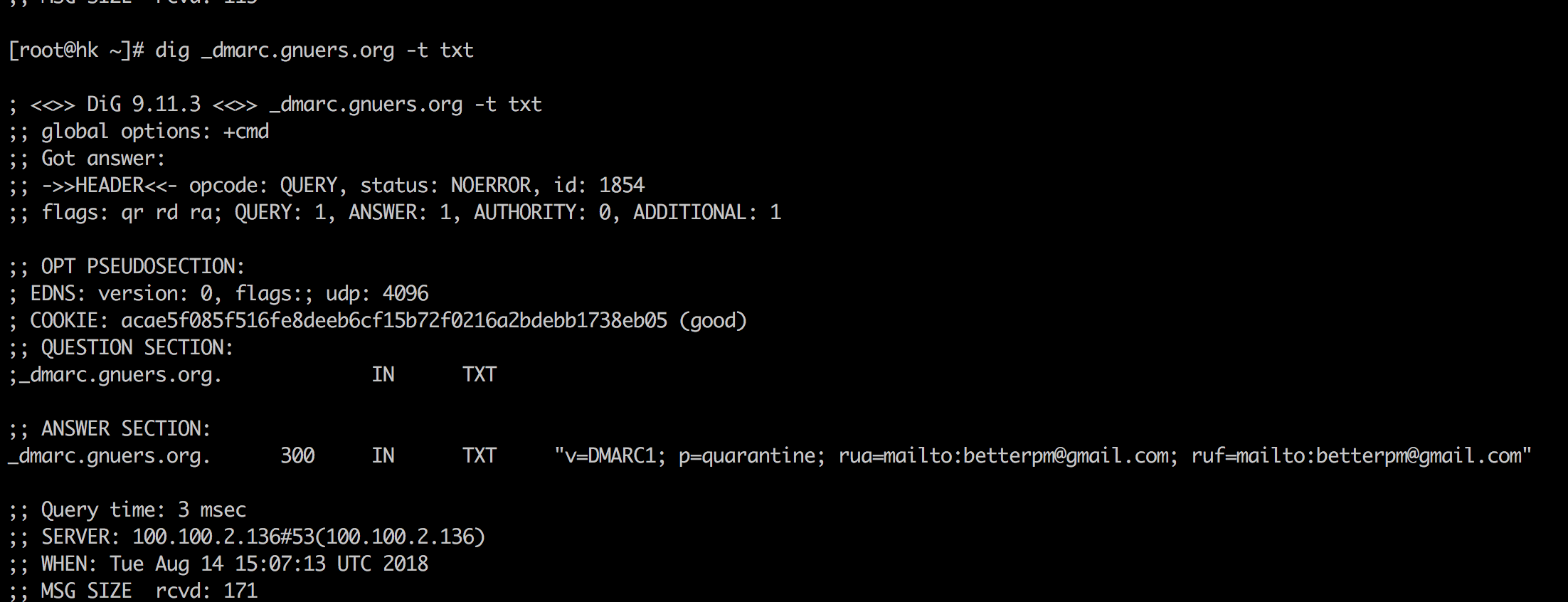
manage_forward_zones: ['gnuers.org']
manage_reverse_zones: ['10.0.0', '192.168', '172.16.123']
- 修改dhcp池配置 /etc/cobbler/dhcp.template
subnet 192.168.117.0 netmask 255.255.255.0 {
option routers 192.168.117.2;
option domain-name-servers 192.168.117.2;
option subnet-mask 255.255.255.0;
range dynamic-bootp 192.168.117.10 192.168.117.20;
- 修改/etc/cobbler/named.template配置,named监听所有IP
options {
listen-on port 53 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { localhost; };
recursion yes;
};
- 获取网络loader(本机有syslinux可以不安装)
systemctl enable cobblerd && systemctl start cobblerd
systemctl enable httpd && systemctl start httpd
systemctl enable rsyncd.service && systemctl start rsyncd.service
systemctl enable tftp && systemctl start tftp
htdigest /etc/cobbler/users.digest "Cobbler" cobbler
配置后可以打开https://192.168.117.134/cobbler_web 登陆web页面
– 确认cobbler配置
- 导入安装镜像
– 挂载ISO到本地并导入cobbler
直接导入会给建立一个默认的profile,使用的ks是 /var/lib/cobbler/kickstarts/sample_end.ks
mount CentOS-7u2.iso /mnt/CentOS7U2
cobbler import --arch=x86_64 --breed=redhat --os-version=rhel7 --path=/mnt/CentOS7U2/ --name=CentOS7U2
cobbler profile list
cobbler profile remove --name CentOS7U2-x86_64
cobbler distro list
cobbler distro remove --name CentOS7U2-x86_64
- 添加自己的profile
– 先配置自己的ks文件,再做profile添加
新增自己修改过的ks文件到var/lib/cobbler/kickstarts/7u2diy.ks
cobbler profile add --name=Centos7U2-DIY --distro=CentOS7U2-x86_64 --kickstart=/var/lib/cobbler/kickstarts/7u2diy.ks
- 设置自动运行的profile
直接修改/var/lib/tftpboot/pxelinux.cfg/default 中ONTIMEOUT为Centos7U2-DIY
- 创建system给特定的机器按指定的模板做自动安装
cobbler system add --name=VMDIY --profile=Centos7U2-DIY --interface=eth0 --mac=00:0c:29:e7:a2:e4 --gateway=192.168.117.2 --ip-address=192.168.117.66 --netmask=255.255.255.0 --static=1 --dns-name=test.alipay.com
mac地址为00:0c:29:e7:a2:e4的服务器开启后会按预设的模板进行装机,并分配指定IP
如果想重装已经装过的服务器,需要先设置netboot标志
cobbler system edit --name=VMDIY --netboot-enabled=1
cobbler sync
KS文件
firewall --disabled
auth --enableshadow --passalgo=sha512
url --url=$tree
text
firstboot --enable
ignoredisk --only-use=sda
keyboard --vckeymap=cn --xlayouts='cn'
lang zh_CN.UTF-8
selinux --disabled
network --bootproto=dhcp --device=eth0 --onboot=yes --ipv6=auto --activate
network --hostname=Centos
rootpw --iscrypted $6$BMgqLp5skYPt6XbU$OQJIOjkvBS2l9Cykbudrtbz8Ym/F9Oc6B9IINXmzunY0pxcWSzzBucTYMV.4bnrZL8.cuhVVPaTRREwksk7Fx.
services --enabled="chronyd"
timezone Asia/Shanghai --isUtc
user --name=pm --password=$6$mYf50m5qC0pf4.ta$0k6i9qdr2I67DAN0C4ToOMF0Kh6mAUVf9A8oNP3WU.VJrcQwpMT1JsyArvopUxCH1Sq/NnAMur8RzTfYQUVux1 --iscrypted --gecos="pm"
bootloader --append="net.ifnames=0 biosdevname=0" --location=mbr --boot-drive=sda
clearpart --none --initlabel
part /home --fstype="ext4" --ondisk=sda --size=8192
part swap --fstype="swap" --ondisk=sda --size=1023
part /boot --fstype="ext4" --ondisk=sda --size=2048
part / --fstype="ext4" --ondisk=sda --size=9214
%packages
@^minimal
@core
chrony
kexec-tools
vim
wget
bind-utils
keepalived
quagga
rsync
%end
%addon com_redhat_kdump --enable --reserve-mb='auto'
%end
%anaconda
pwpolicy root --minlen=6 --minquality=1 --notstrict --nochanges --notempty
pwpolicy user --minlen=6 --minquality=1 --notstrict --nochanges --emptyok
pwpolicy luks --minlen=6 --minquality=1 --notstrict --nochanges --notempty
%end
%post --interpreter=/bin/bash
cd /etc/yum.repos.d/ && rm -frv *
/bin/cat </etc/yum.repos.d/CentOS-Base.repo
[base]
name=CentOS-$releasever - Base - mirrors.aliyun.com
failovermethod=priority
baseurl=http://mirrors.aliyun.com/centos/$releasever/os/$basearch/
gpgcheck=1
gpgkey=http://mirrors.aliyun.com/centos/RPM-GPG-KEY-CentOS-7
[updates]
name=CentOS-$releasever - Updates - mirrors.aliyun.com
failovermethod=priority
baseurl=http://mirrors.aliyun.com/centos/$releasever/updates/$basearch/
gpgcheck=1
gpgkey=http://mirrors.aliyun.com/centos/RPM-GPG-KEY-CentOS-7
[extras]
name=CentOS-$releasever - Extras - mirrors.aliyun.com
failovermethod=priority
baseurl=http://mirrors.aliyun.com/centos/$releasever/extras/$basearch/
gpgcheck=1
gpgkey=http://mirrors.aliyun.com/centos/RPM-GPG-KEY-CentOS-7
[centosplus]
name=CentOS-$releasever - Plus - mirrors.aliyun.com
failovermethod=priority
baseurl=http://mirrors.aliyun.com/centos/$releasever/centosplus/$basearch/
gpgcheck=1
enabled=0
gpgkey=http://mirrors.aliyun.com/centos/RPM-GPG-KEY-CentOS-7
[contrib]
name=CentOS-$releasever - Contrib - mirrors.aliyun.com
failovermethod=priority
baseurl=http://mirrors.aliyun.com/centos/$releasever/contrib/$basearch/
gpgcheck=1
enabled=0
gpgkey=http://mirrors.aliyun.com/centos/RPM-GPG-KEY-CentOS-7
)2>&1 >> /root/post-install.log
%end
命令说明
- 镜像相关的操作
[root@Centos kickstarts]# cobbler distro ##
usage
=====
cobbler distro add
cobbler distro copy
cobbler distro edit
cobbler distro find
cobbler distro list
cobbler distro remove
cobbler distro rename
cobbler distro report
- 安装模板配置
[root@Centos kickstarts]# cobbler profile
usage
=====
cobbler profile add
cobbler profile copy
cobbler profile dumpvars
cobbler profile edit
cobbler profile find
cobbler profile getks
cobbler profile list
cobbler profile remove
cobbler profile rename
cobbler profile report
- 添加发型版支持
编辑 /var/lib/cobbler/distro_signatures.json
[root@Centos kickstarts]# cobbler signature reload
usage
=====
cobbler signature reload
cobbler signature report
cobbler signature update
遇到的问题
- 内存不足,VM 只分了1G 内存
mount: wrong fs type, bad option, bad superblock on /dev/loop0
missing codepage or helper program, or other error
in some cases useful info is found in syslog - try
dmesg | tail or so
umount: /run/initramfs/squashfs: not mounted
/sbin/dmsquash-live-root: line 273: printf: write error: no space left on device
- 开启gpxe后无法安装
因为渲染出来的启动菜单的参数有问题,启动不了的时候都可以看看pxe的菜单内的参数是否正常 /var/lib/tftpboot/pxelinux.cfg/default
参考
- https://yhuan.online/index.php/automation/cobbler.html
- https://wsgzao.github.io/post/cobbler/
- http://cobbler.github.io/manuals/quickstart/
- http://cobbler.github.io/manuals/2.8.0/